Code injection, often referred to as remote code execution (RCE), is an attack perpetrated by an attacker's ability to inject and execute malicious code into an application; injection attack. This foreign code is capable of violating data security, compromising database integrity or private properties. In many cases, it can bypass the authentication check, and these attacks are usually associated with applications whose execution depends on user input.
ContentsTypes of Code InjectionsHow SQL Injections WorkWhat SQL Injection Can DoHow to Prevent SQL InjectionsScript InjectionHow to Prevent Script InjectionsConclusionTypically, applications are more vulnerable if code is executed without first going through validation. A simple case of vulnerable code is shown below.
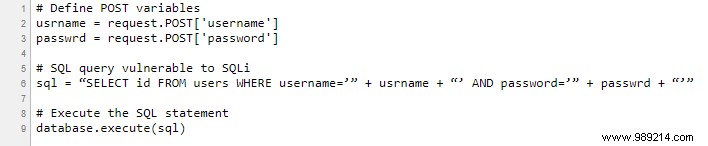
In the code above, the attacker could insert a payload that would modify the SQL statement executed by the database server. An example would set the password field to:
password’ OR 1=1
This automatically causes the following statement to be executed on the database server:
SELECT id FROM users WHERE username='username' AND password='password' OR 1=1
This is the most common type of code injection. Considering that SQL is the language used to manipulate data stored in relational database management systems (RDBMS), an attack with the power to give and execute SQL statements can be used to access, modify and even delete data.
This can give the attacker the ability to bypass authentication, have full disclosure of data stored in the database, compromise data integrity and cause repudiation issues, alter balances and cancel transactions.
There are a few steps to make your apps less vulnerable, but before each step, it's best to assume that all user-submitted data is bad and don't trust anyone. Then you can consider the following:
This security vulnerability is a threat that allows an attacker to inject malicious code directly into web forms of data-driven websites through user interface elements. This attack is often called Cross-Site Scripting or XSS. the