So what exactly did the hackers get? Every hack is different, but they almost certainly obtained your email address, user information, records of your site activity, and possibly much more damaging stuff. Good news though:a lot of the most sensitive data was probably encrypted. There's also a good chance he wasn't encrypted, but let's take the best data theft scenario:your information was stolen, but the sensitive stuff was encrypted with AES-256. Is it safe?
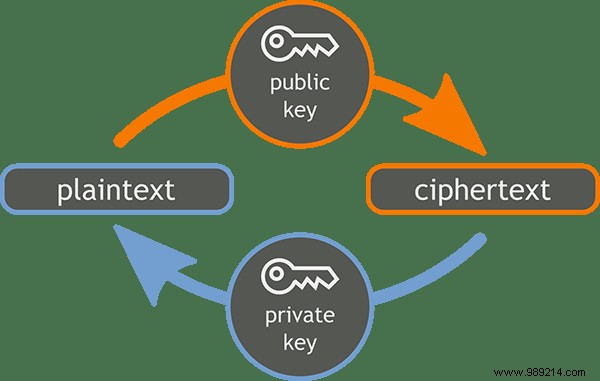
The short answer is yes:encryption can be cracked. A brute force approach, which is basically making lots and lots of guesses until you're proven to be right, would certainly find the right answer, given enough time and computing power. Given our current capabilities, brute forcing AES-256 could take up to 3 sexdecillion (3×10 51 ) years, and similar numbers could be associated with many widely used encryption algorithms. In the future, quantum computers and other advancements may significantly reduce the security of encryption, but until then it is effectively impenetrable.
But that doesn't make encryption foolproof. Attackers are well aware that encrypted data is useless without keys, so what are they going after? The keys. The most catastrophic data breach possible is one in which encrypted data and decryption keys are stolen. If data security is properly implemented, the keys (multiple keys for different data, probably per user) will be stored securely in a separate location from the data and should probably be encrypted themselves. Additionally, the keys will need to be decrypted and retrieved securely whenever certain data needs to be decrypted, so that attackers cannot intercept it. On top of all that, the keys should probably be changed regularly.
If the site your information was stolen from did all of this, the attackers probably didn't catch the keys and your data is safe until the sun goes out or we invent much more powerful computers. . But how likely are the sites to actually do this, and how much of your data is encrypted, even in the best-case scenario?
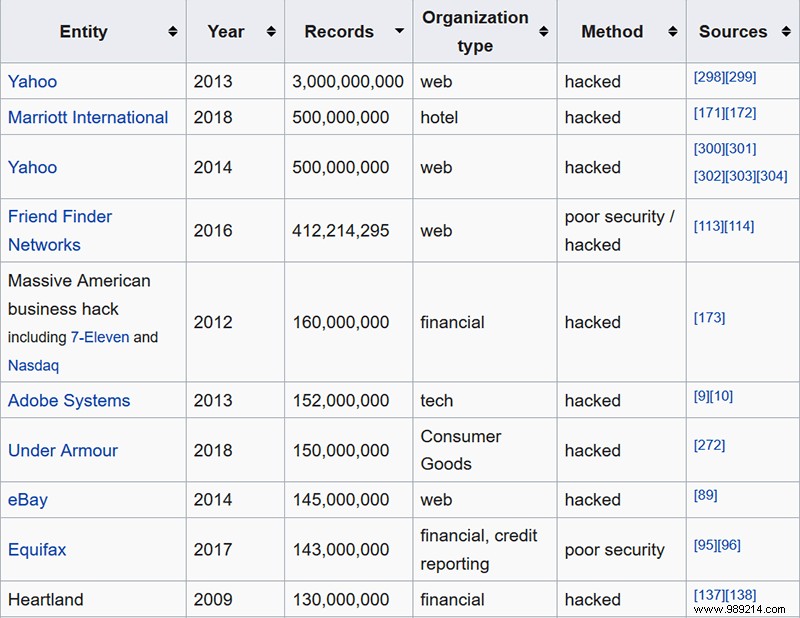
Remember that list of data breaches at the start of this article? Let's check them again.
This list can get very, very long, but you get the idea:basically, the only thing that's encrypted on most sites is your password (which is actually hashed) and payment information. Unless it's a site that deals with a lot of sensitive information or has something high security, your data breach likely exposed a good chunk of your PII (personally identifiable information). This is mainly because encrypting and decrypting things takes a lot more computing power, time, effort and money than just storing them in plain text and serving them directly to you.
Even the encrypted elements of these hacks were not always safe. Yahoo and MyFitnessPal used bcrypt for their passwords, which is a strong encryption standard, but they also used MD-5 and SHA-1 respectively, mainly for older accounts. These are much weaker hashing algorithms. MySpace just used unsalted SHA-1 for everything, which makes sense, but also means your password has almost definitely been leaked. Yahoo also didn't say if they salted their passwords in 2013 (they probably didn't), which makes them quite vulnerable to hacking.
Marriott even lost 5.25 million plaintext passport numbers, which is not good. They clearly knew they would have to put a number on them (20 million others were, after all), but let 20% of their customers down. They also encrypted credit card numbers:but are not sure if the hackers got the key or not.
The moral of the story:most of your data is not encrypted, even what you really think should be.
That's right, so you were using a website with fantastic security that encrypted every last bit of your information. These do exist – many file storage sites (Dropbox, Google Drive) will encrypt your files in their database, for example. If so, as long as their key storage game was solid and their security experts did a good job with the developers, chances are your data will remain intact until the device thermally dies. universe.
The more likely scenario, however, is that much of your information has not been encrypted, and even sensitive information may have been improperly hashed or encrypted with the key somewhere in the database or in the system. of files. There's not much you can do about this, as you need to provide companies with your data to use their services, but you can try to keep it to a minimum – and don't reuse passwords !
And don't forget to check HaveIBeenPwned to see if your data has come up in breaches.
Image Credits:Public Key Encryption Keys, Data Security Breach, Orange Blue Public Key Cryptography