Each application has its own reading area:a “sandbox”. If the app wants to access outside of its sandbox, it needs to ask the operating system for permission. Depending on the sandbox settings, the operating system will deny or approve the application request while providing the least specific information possible to complete the request.
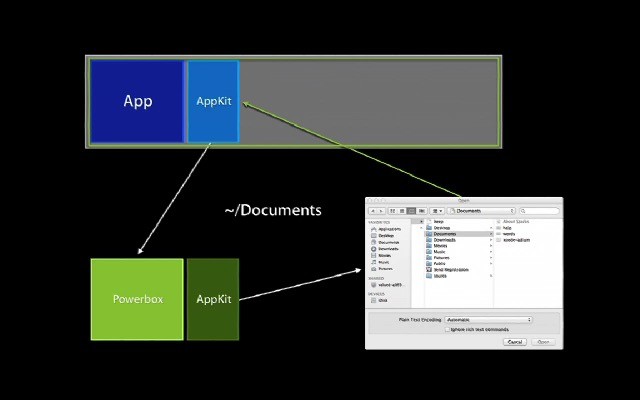
The application cannot directly see what is happening in Powerbox. Only the opened or saved file will be accessible to the application. This way, applications can perform critical functions without unnecessary risk.
This functionality is activated by a right (more precisely com.apple.security.files.user-selected.read-write ). Application developers define rights that declare what an application does. Based on the declared rights, the operating system allows the application an appropriately limited level of functionality.
This thought process underlies the entire app sandboxing model and mechanism:apps must declare their intent and seek permission from an OS-level maintainer to do something dangerous. .
As of June 1, 2012, all third-party apps distributed through the Mac App Store must be sandboxed. Although sandboxing enables a wide range of app functionality, you'll find that Mac App Store apps are often more limited than their non-sandbox components. Some developers even maintain two versions:a full app for direct download and a wrapped version for the Mac App Store. Thanks to the greater complexity of sandbox development, adding new functionality to an application is more difficult – if that functionality is even allowed by the operating system, that is.
While sandboxed apps can benefit from Mac App Store distribution, you can guess how valuable we think that is. Sandboxing can also be extended with security permissions. Although an app cannot enable accessibility permissions for itself, it can prompt the user to do so.
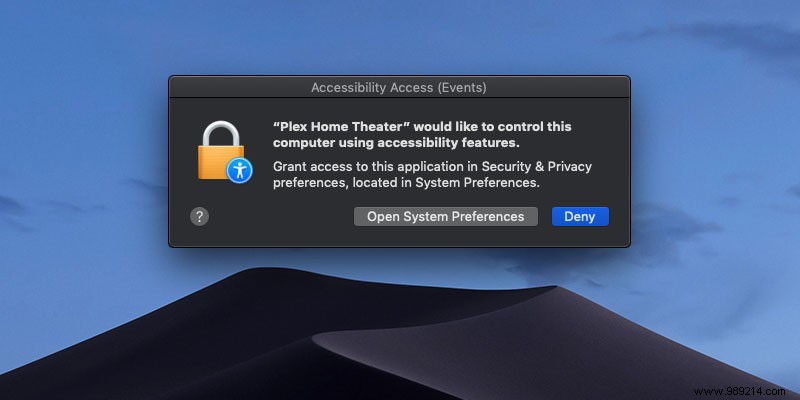
To see which of your apps are sandboxed, open Activity Monitor and right-click column headings to add “Sandboxed” to the window.
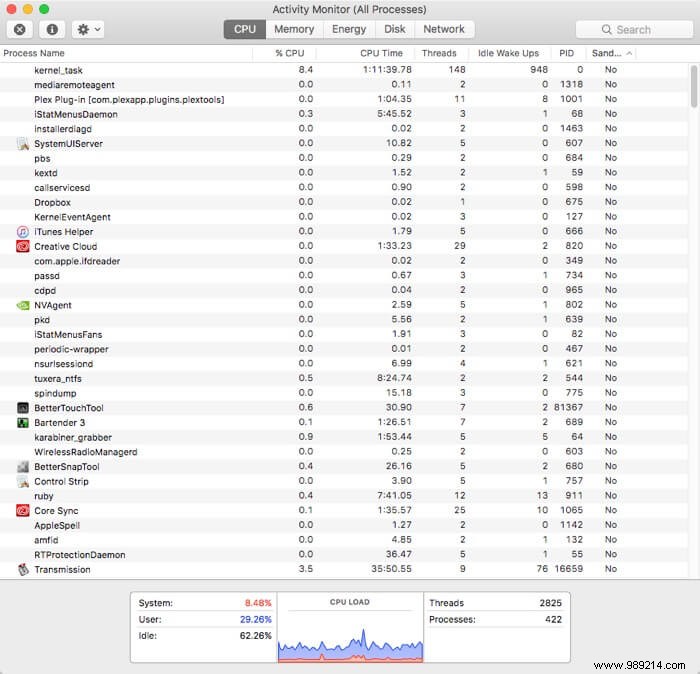
Some applications simply can never exist in a sandbox. In fact, a variety of valuable use cases are avoided by sandboxing. Sandboxing prevents communication, observation, or modification between apps, which severely limits how apps can interact. System-wide shortcuts like TextExpander are completely forbidden, as this level of functionality could be allowed by the sandbox.
Although promising, macOS application sandboxing was not well executed. This limited the unique selling points of Mac apps, like speed and enhanced functionality. Applications running outside of the sandbox are almost always better performing and faster. From this power user's perspective, my most-used apps aren't sandboxed. Applications like TextExpander, SnagIt and TotalFinder are all essential to my daily work. To avoid similar widespread avoidance, future security systems need flexibility and power balanced with transparency.
Image credit:Apple